
Every day, businesses and organizations across industries rely on Microsoft Teams to collaborate, share ideas, and stay connected no matter where they are. With security at the core of our platform, we’ve designed Microsoft Teams to help organizations manage meetings with confidence, prevent disruptions, and protect sensitive conversations.
At the same time, the rapid advancements in AI and large language models (LLMs) have presented new challenges in controlling who—or what—enters a meeting. As automated bots and AI-driven threats become more sophisticated, preventing unauthorized access requires a proactive approach. While Microsoft Teams is built with powerful protections, staying informed and leveraging the right security tools is essential to keeping your meetings secure.
In response to growing concerns around meeting security, many IT administrators take a cautious approach by disabling all external access to virtual meetings across their organization. While this may reduce immediate risk, it can also limit the effectiveness of virtual meetings as a tool for external collaboration. Rather than choosing between security and collaboration, organizations need solutions that deliver both. This blog explores best practices for protecting Teams meetings from unauthorized access while still enabling the open, productive collaboration today’s teams depend on.
Table of Contents
ToggleManage meeting access and join experience
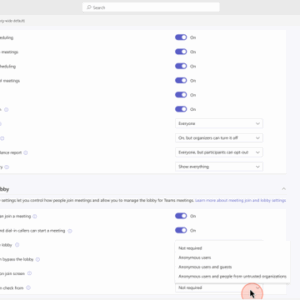
One of the most important ways to secure your meetings is by controlling access to the meeting and verifying attendees. The first step to managing meeting access is to enable the meeting lobby. The Teams meeting lobby prevents certain types of participants from directly joining a meeting until a meeting organizer admits them. When a participant goes to the lobby, organizers are notified and can admit them to the meeting or not.
Meeting organizers can choose in meeting options who can bypass the lobby and join the meeting directly, as well as which meeting roles can admit participants waiting in the lobby. Organizers can enable lobby for all meetings by setting the “Who can bypass the lobby” control to a value of “people in my org.” This will result in users outside of your organization, including bots, joining as anonymous users and waiting in the lobby, they then must be admitted to the meeting.
Meeting organizers can also enable the setting for “Who can admit from lobby” to “Organizer and co-organizer only” to reduce the number of participants who can admit from the lobby.
After enabling lobby controls, the next step is to employ direct blocking of external participants. IT administrators can use the external access feature to block specific external domains, including known bot domains. This prevents participants from these domains from joining meetings. External access allows for a more granular way to control who enters meetings, unlike the control to block all anonymous or unverified users from joining meetings at the organization level, or applied to specific organizers or groups. By toggling the “Anonymous users can join a meeting” and “Anonymous users can join a meeting unverified” to the “Off” state, this can help prevent unauthorized participants—including external recording bots—from joining meetings, but it will limit the overall effectiveness of Microsoft Teams for external collaboration.
Additionally, IT administrators can enable a CAPTCHA-based human verification test and apply it to anonymous and non-federated users. Once set, any anonymous user that attempts to join the meeting will be required to pass the CAPTCHA test before proceeding.
As an advanced measure, email verification of external attendees is available to meeting organizers with a Teams Premium license. With email verification, meeting organizers can require external participants to verify their email addresses with a verification code before joining the meeting. Once verified, participants will appear in the meeting with the ‘Email verified’ label, offering a more reliable way for organizers to manage external participants.
Protect Sensitive Information
Now that you can confidently control who enters your meeting, let’s dive into the safeguards designed to protect your data, privacy, and sensitive information during the meeting. A Microsoft Teams Premium subscription delivers advanced protection for your meeting data through watermarking, end-to-end encryption, granular meeting controls, and sensitivity labels.
First, let’s look at watermarking. Meeting watermarks can be enabled for both content shared on screen and for attendee video. When you apply a watermark, participants will see their own email address overlaid across shared content in the meeting window. This deters people from taking unauthorized screenshots of shared content.
For highly confidential meetings, end-to-end encryption (E2EE) helps add an additional layer of privacy where only the participants can hear or see the communication. No other party—including Microsoft—has access to the decrypted conversation. The E2EE works on top of industry-standard encryption in transit and at rest always provided by Teams.
Teams Premium also delivers more granular controls for meeting activity and access to meeting artifacts.
- Manage who can record and transcribe meetings. Meeting organizers can manage which roles can initiate recording and transcription for a meeting. Learn more.
- Block copying or forwarding of live captions, transcript, and recap for meetings. Meeting organizers can block participants’ ability to copy the meeting chat, live captions, live transcript, or any insights generated from intelligent meeting recap. Learn more.
- Prevent users from sharing external content in meetings. IT administrators can control whether users in your org with a Teams Premium license can share content when attending external Teams meetings. Learn more.
- Organization templates. IT administrators can use organization templates to enforce meeting options or to set defaults. Each template option can be locked so the meeting organizer can’t change it, or can be left unlocked for the meeting organizer to change if needed. Learn more.
Sensitivity labels are used to classify and protect sensitive information within the organization. They help ensure that only authorized individuals can access certain content, including meetings. Sensitivity labels can be applied to meetings to restrict access based on the classification of the information being discussed. This can include preventing external participants from joining or limiting the ability to record the meeting.
Depending on how an organization configures its labels, Teams Premium applies a templatized set of designated meeting options to enhance security and compliance.
Those options include:
- Who needs to wait in the meeting lobby
- Who needs to ask to join the meeting
- Calendar labels, for example, “Do not forward”
- Enforcing automatic recording
- Restricted copying and pasting from the meeting chat
- Advanced encryption control for audio-video streams
- Watermarking on live content and video
User education
We recognize that security, compliance, and privacy have never been more important, and we’re committed to delivering solutions that are secure by design. But protecting meetings isn’t just up to us; it’s a shared responsibility. When it comes to meeting security, the best asset is educated users who employ the security features effectively. Training your team on best practices is critical, tips like training users to deny unverified participants from the lobby, ensuring organizers check names before admitting participants, and familiarizing everyone with the security measures outlined in this blog are essential to maximizing your organization’s security.
No matter how you’re using Teams in this rapidly evolving landscape, we remain committed to continuing to learn and get better each day as we work to help you keep all your conversations private and secure. Our approach to these important issues is designed to give you the control and manageability you need to have peace of mind against dynamic threats. Please check out the Security guide for Microsoft Teams and the Microsoft Trust Center for more details.
Source link

roosho.
I am Rakib Raihan RooSho, Jack of all IT Trades. You got it right. Good for nothing. I try a lot of things and fail more than that. That's how I learn. Whenever I succeed, I note that in my cookbook. Eventually, that became my blog.




No Comment! Be the first one.